On February 26, 2024, the National Institute of Standards and Technology (NIST) released the long-awaited second version of the Cybersecurity Framework (CSF). Dubbed “CSF 2.0,” it contains a few significant changes:
- Creation of a new “Govern” function.
- Increased acknowledgement of supply chain and vendor security.
- An intentional effort to reframe the CSF to make it more accessible to and usable by smaller organizations.
As we noted in a July 2023 blog post, NIST was required by the White House’s National Cybersecurity Strategy to update the CSF by the first quarter of fiscal year 2025. The publication of CSF 2.0 puts NIST far ahead of schedule.
The Govern function is a gamechanger
The creation of the Govern function and its interconnectedness with all the other functions mark the biggest difference between NIST CSF 1.1 and CSF 2.0. This new Govern function requires an organization to “establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.” As background, CSF 1.0 and 1.1 were built around five core functions – Identify, Protect, Detect, Respond and Recover – that CSF 1.1 stated “should be performed concurrently and continuously to form an operational culture that addresses the dynamic cybersecurity risk.” CSF 2.0 is similarly built around core functions, providing the flexibility of “a common language and systematic methodology,” with room to tailor practices to a company’s specific circumstances. Each function is then broken down into categories and subcategories of actions, each providing more granular detail for operationalizing CSF 2.0.
Although the Govern function is conceptualized as a CSF core function in CSF 2.0, Govern transcends the other functions, weaving through a layer of organizational and strategic considerations necessary to operationalize the other functions. Indeed, NIST itself has created a graphic of the functions as a wheel, with Govern closer to the center because “it informs how an organization will implement the other five functions”:
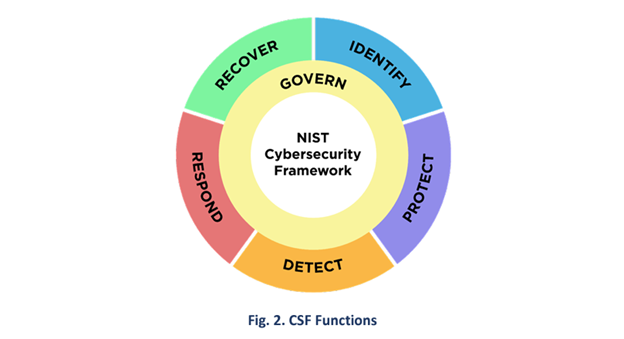
The Govern function addresses the need for an overarching governance structure across an organization that can streamline policies, practices and norms while “support[ing] organizational risk communication with executives.” The Govern function explicitly notes the importance of integrating cybersecurity into an organization’s enterprise risk management. For public companies, this dovetails with the Securities and Exchange Commission’s new required cybersecurity disclosure in annual reports, which requires registrants to (among other things) describe the integration of cybersecurity risk management into an organization’s overall risk management.
The Govern function also focuses heavily on supply chain management and the role of third parties in an organization’s security, including a Cybersecurity Supply Chain Risk Management category (GV.SC). Other Govern categories include:
- Organizational Context (GV.OC), which deals with an institutional understanding of the “circumstances … surrounding the organization’s cybersecurity risk management decisions.”
- Risk Management Strategy (GV.RM), which focuses on the support of operational risk decisions via the “organization’s priorities, constraints, risk tolerance and appetite statements, and assumptions.”
- Roles, Responsibilities and Authorities (GV.RR), which highlights the establishment of “[c]ybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement.”
- Policy (GV.PO), which focuses on the use of an “organizational cybersecurity policy” and making sure it is “established, communicated, and enforced.”
- Oversight (GV.OV), which addresses the need for “organization-wide cybersecurity risk management activities and performance” to be “used to inform, improve, and adjust the risk management strategy.”
Third-party risk and supply chain management
GV.SC details subcategories of activities to help organizations integrate supply chain management and security into the broader governance structure. This category reflects a slew of public comments on the initial drafts of CSF 2.0 requesting that NIST address the unique risks and challenges posed with respect to third-party entities.
GV.SC also breaks down subcategories to help organizations tackle supply chain risk. CSF 2.0 suggests that organizations should have a supply chain vendor risk management program – and they should ensure that cybersecurity roles and responsibilities for supplies and other third parties are communicated and coordinated clearly. Additionally, CSF 2.0 indicates that cybersecurity supply chain management should be integrated into the overall enterprise risk management. Suppliers should be categorized by criticality, and organizations should incorporate cybersecurity risk requirements into contracts or other agreements with suppliers and third parties. Organizations should engage in due diligence of suppliers and third parties, and they should incorporate relevant suppliers and third parties into incident response training and planning.
Making CSF 2.0 more accessible
NIST’s CSF 1.1 originally was intended to be used by large organizations, generally those in critical infrastructure sectors. However, CSF 2.0 recognizes the utility and importance of such a cybersecurity framework for organizations of all sizes. CSF 2.0 includes CSF tiers as an appendix, which provides various breakdowns of an organization’s level of compliance: Tier 1 (Partial), Tier 2 (Risk-Informed), Tier 3 (Repeatable) and Tier 4 (Adaptive). These tiers give organizations of any size internal benchmarks to assess compliance – and help organizations scale the adoption of CSF appropriate to their size, sector and resources.
Wrapping up
NIST continues to provide a usable and flexible, yet informative, set of guidelines to help organizations create and operationalize a cybersecurity function. CSF 2.0 updates the framework to address the growing importance of cybersecurity in an organization’s enterprise risk management, the criticality of third parties and suppliers in an organization’s cybersecurity risk management, and the need for organizations of all shapes and sizes to prioritize cybersecurity in whatever way is appropriate for them.
